How to mitigate Apache Log4j exploit on VMware UNIFIED ACCESS GATEWAY
For VMware UAG thats is in most cases exposed to internet, its necessary to apply WORKAROUND for CVE-2021-44228 to Unified Access Gateway version 2009 through to 2111.
Firtsly we need enable SSH login to the UAG Appliacne, which is by default permited.
Connect from VMware vCenter console to the UAG VA and run “ vi /etc/ssh/sshd_config“ and change the PermitRootLogin no > PermitRootLogin yes and save the file, after you must restart sshd service with command „service sshd restart “ dont forget DISABLE the SSH connection after your work :)))
UPDATED 22. 12. 2021
How to workaround Apache Log4j on UAG:
(tested on euc-unified-access-gateway-v3.9.0.0-15751318)
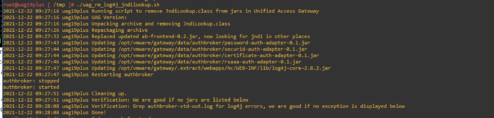
Download and copy the script uag_rm_log4j_jndilookup.sh to the UAG VA, you can use WinSCP, and copy file to the /tmp folder.
- SSH into UAG console as root user and cd to the directory in which the above script is located.
- Set executable permission for the above script „chmod +x uag_rm_log4j_jndilookup.sh„
- Run the script to remove all the occurrences of log4j’s JndiLookup.class
„./uag_rm_log4j_jndilookup.sh„
- If the UAG version is between 2009 and 2111 it is also necessary to set the -Dlog4j2.formatMsgNoLookups=true option on the authbroker service with the following commands. Note the space between „s/java /java“ and a space after „true /“ in the command, these are important to ensure the command works correctly and doesn’t attempt to modify the wrong lines in the configuration file.
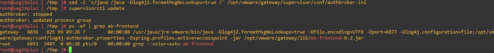
„sed -i ‚s/java /java -Dlog4j2.formatMsgNoLookups=true /‘ /opt/vmware/gateway/supervisor/conf/authbroker.ini„
- and run update of supervisorctl:
„supervisorctl update“ - verify that the new setting has taken affect by running the following command and checking that the process command parameters include -Dlog4j2.formatMsgNoLookups=true:
„ps -ef | grep ab-frontend„
this workaround is known to be insufficient.
see the revised instructions.
https://kb.vmware.com/s/article/87092
Hi, Jan thank you very much for your response, the post was UPDATED to latest workaround from VMware and tested in my lab on euc-unified-access-gateway-v3.9.0.0-15751318